tr

Is a Social Science Degree Worth It in 2025?
Delving into the Value of Social Science Education In the modern landscape, where technology and data reign supreme, the relevance of social science degrees has often been put under scrutiny. With this comprehensive analysis, we aim to shed light on the worthiness of pursuing a social science degree and unveil the potential it holds for…
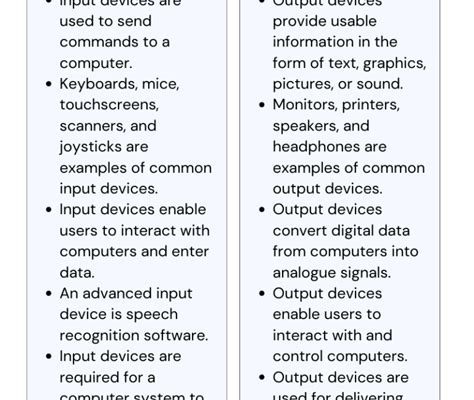
Input vs Output Devices: Ultimate Guide 2025
Definition Input Devices: Devices that allow users to interact with and provide data or signals to a computer system. Examples include keyboards, mice, and scanners. Output Devices: Devices that display or communicate information from a computer system. Examples include monitors, printers, and speakers. Functionality and Characteristics Input Devices Function: Collect and relay data or signals…
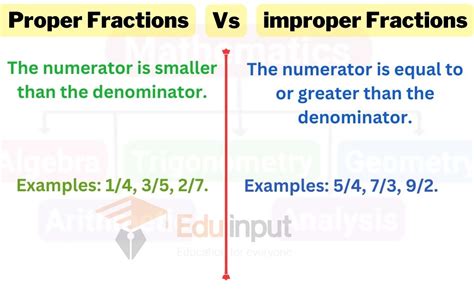
2025: Proper vs. Improper Fractions: A Comprehensive Guide
Introduction In the realm of mathematics, fractions play a pivotal role in representing parts of a whole. Understanding the distinction between proper and improper fractions is essential for students, mathematicians, and anyone who encounters fractions in everyday life. This article provides a comprehensive guide to proper and improper fractions, exploring their definitions, examples, operations, and…

1001 Control System MCQs with Answers for 2025 Success
Introduction Control systems are ubiquitous in modern industry, from manufacturing and transportation to healthcare and energy. They play a critical role in ensuring the efficient, reliable, and safe operation of complex systems. To excel in this field, a thorough understanding of control system concepts is essential. The Power of MCQs Multiple-choice questions (MCQs) provide an…
7 Products You Can’t Sell Online in 2025 VS. 8 You Can
Introduction The e-commerce market is booming, with sales expected to reach \$6.54 trillion by 2025. However, not all products can be sold online. Some items are simply too large, fragile, or perishable to be shipped safely. Others are restricted by law or regulation. 7 Products that Cannot Be Sold Online 1. Large Appliances Large appliances,…
Further Enhancements
Grab Your Air Ticket to London with Singapore Airlines: The Ultimate 2025 Flight Experience Indulge in an unparalleled air travel experience with Singapore Airlines, the world’s leading carrier, as you embark on your journey to the vibrant metropolis of London. World-Class Amenities at Your Fingertips Exclusive Suites: Experience unparalleled comfort and privacy in our luxurious…

POSB Kaki Bukit Branch Opening Hours: 2025 and Beyond
Hours of Operation: Day Time Monday 9:00 AM – 4:00 PM Tuesday 9:00 AM – 4:00 PM Wednesday 9:00 AM – 4:00 PM Thursday 9:00 AM – 4:00 PM Friday 9:00 AM – 4:00 PM Saturday Closed Sunday Closed — Transitioning to a Digital-First Future In the rapidly evolving landscape of banking, digital channels are…

Come to Me, All Who Are Weary: Finding Rest in 2025
Introduction: The Heavy Burden of Life In the face of life’s relentless demands and the weight of our own struggles, we may feel overwhelmed and lost. The invitation of Jesus, “Come to me, all who are weary and heavy laden, and I will give you rest” (Matthew 11:28), offers solace and hope amidst the turmoil….

Coconut Water: The Cure-All for Cough and Fever in 2025
Coconut water has been touted as a miracle cure for various ailments, including cough and fever. But is there any scientific evidence to support these claims? Let’s take a closer look at the potential benefits of coconut water for these common conditions. 1. Coconut Water’s Benefits for Cough 1.1. Immune Booster: Coconut water is rich…

How Much Do Freelance Pentesters Make in 2025?
Introduction The demand for freelance penetration testers (pentesters) has skyrocketed as organizations increasingly recognize the importance of cybersecurity. These highly skilled professionals play a crucial role in identifying and mitigating vulnerabilities in IT systems, ensuring the protection of sensitive data and critical assets. In this article, we will explore the factors that influence the earning…